08. Vulnerability Management
Vulnerability Management
Vulnerability Management - Overview
ND545 C1 L3 07 Vulnerability Management - Overview
Vulnerability
NIST defines vulnerability as a “Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat.”
In IT, vulnerabilities are inevitable. No matter how hard we try, there will always be weaknesses in software, operating systems and networks. Most vulnerabilities are minor or the path to use or exploit them to cause harm is long and difficult. We need to pay attention and know what vulnerabilities need to be fixed right away and which ones can maybe wait.
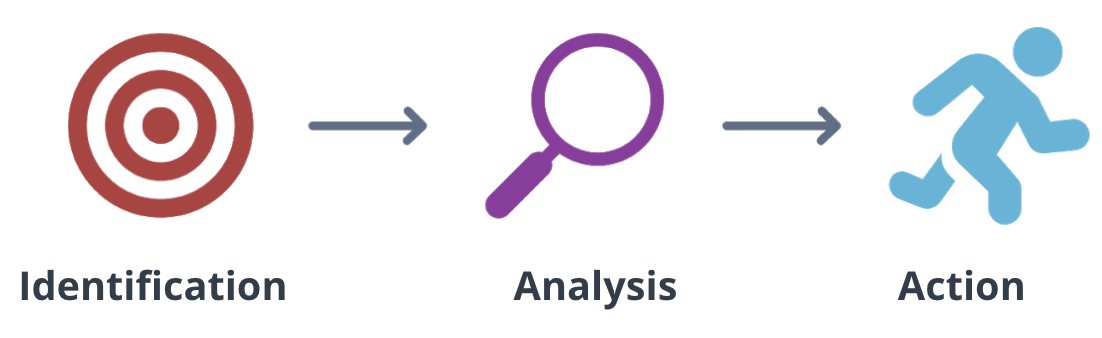
Vulnerability management
Vulnerability management
Vulnerability management starts with Identifying the vulnerability, Analyzing it, and then taking action. Identification is just knowing that something could be a problem. Analysis is the decision - what to do about it, and taking action is implementing the decision
Vulnerability Management - Identification
ND545 C1 L3 08 Vulnerability Management - Identification
Identification summary
Identification is finding vulnerabilities.
Examples of vulnerabilities with cars:
- Bald tires
- Old breaks
- Manufacturer recall
Examples of vulnerabilities in information technology.
- Code / Software apps
- Networks
- Unpatched systems
There’s a large community dedicated to finding vulnerabilities and letting others know.
Sources include:
- Vendors
- Vulnerability lists & databases
NIST National Vulnerability Database (NVD) - https://nvd.nist.gov/
MITRE Common Vulnerabilities and Exposures (CVE) list - https://cve.mitre.org/about/index.html
- Bug Bounties
- Security assessments
Vulnerability Management - Analysis and Action
ND545 C1 L3 09 Vulnerability Management - Analysis And Action
Analysis and action summary
Analysis is studying the vulnerability and deciding a course of action.
The CVE and NVD websites provide vulnerability ratings. The manufacture may also tell you their idea of the risk.
Taking Action is doing something about the vulnerability once you’ve analyzed its risks and the benefits of applying a fix.
** Zero-Day (0-Day) Vulnerabilities** are vulnerabilities that have no notification to the manufacturer or public.
Vulnerability Information Resources
There are two resources for discovering and analyzing vulnerabilities: the MITRE Common Vulnerabilities and Exposures (CVE) list and the
NIST National Vulnerability Database (NVD). They are commonly used in the cybersecurity world and you will see them very often. In this section, we will only cover them at a high-level.
ND545 C1 L3 10 Identifying Software Vulnerabilities Exercise Video
Summary
CVE is “a list of common identifiers for publicly known cybersecurity vulnerabilities.” It was started over 20 years ago to create a common language and naming convention for all vulnerabilities. In the early days, manufactures would have their own names and identification numbers, which became very confusing.
Description from the CVE website: “The process of creating a CVE Entry begins with the discovery of a potential security vulnerability.
The information is then assigned a CVE ID by a CVE Numbering Authority (CNA), the CNA writes the Description and adds References, and then the completed CVE Entry is added to the CVE List and posted on the CVE website by the CVE Team”
The NVD is the U.S. government repository of standards-based vulnerability management data. They perform analysis on CVEs that have been published to the CVE Dictionary.
New terms
- Vulnerability: A weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat.
Source: https://csrc.nist.gov/glossary
Further research
- MITRE Common Vulnerabilities and Enumeration - https://cve.mitre.org
- NIST National Vulnerability Database - https://nvd.nist.gov/general